The estimated 200,000 computers crippled worldwide by Friday’s mammoth ransomware attack could be only the tip of the iceberg, security experts said Sunday.
The apparently random attack, called “WannaCry,” hit on Friday and spread like wildfire before a British malware researcher identified as Marcus Hutchins was able to halt it temporarily on Saturday, when workers in many companies weren’t in their offices.
That means an untold number of other infected systems could still be waiting to be discovered when people return to work on Monday and fire up their computers.
And there’s worse news: At least two new variations of the malware have already been detected.
The malware spreads as a worm — scanning other computers linked to any machine or system it infects for the same defect and leaping onto them — through a vulnerability in Microsoft systems, particularly on outdated software like Windows XP or Windows Server 2003.
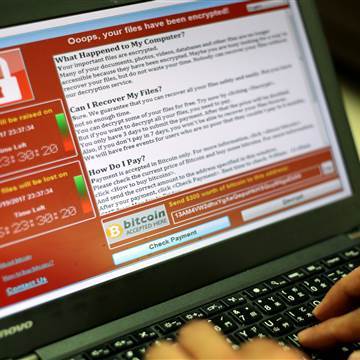
The malware includes an encryption package that automatically downloads itself to infected computers, locking up nearly all of the machines’ files and demanding payment of $300 to $600 for a key to unlock them.
All it takes is for one computer on a network to be infected for all of the computers on that network to be compromised.
While Microsoft had stopped supporting older versions of Windows, it said it is pushing out special automatic updates to those systems to block the worm.


Unfortunately, those so-called legacy systems are disproportionately used by smaller companies with small technology staffs, which are unlikely to have blocked the infection before Microsoft’s patch began rolling out, the cybersecurity firm Proofpoint Inc. said.
Even then, Microsoft’s updates can be loaded only if a computer is powered back on — something that won’t happen for the first time at potentially thousands of companies until Monday.
“I am worried about how the numbers will continue to grow when people go to work and turn [on] their machines,” Rob Wainwright, director of the European investigative agency Europol, told NBC News partner ITV on Sunday.
Complicating matters is that new versions of the worm launched over the weekend are recoded to skirt the temporary fix, according to security specialists.
“Organizations need to update their software,” Kristy Campbell, chief spokeswoman for the cybersecurity firm Proofpoint Inc., told NBC News on Sunday. “Those who do not will see their systems affected at an increasing rate by different variants of this malware.”
Tarah Wheeler, senior director of engineering and for the security company Symantec, tweeted Sunday: “Round two, gentlefolk. Let’s rock.”
Kurtis Baron, a security specialist with consultants Fidus Information Security — who confirmed that his friend Hutchins was the hero researcher who stopped the initial attack — told NBC News on Sunday that he “doesn’t doubt for a moment that Marcus, and people like him, will be getting ready to deal with a second attack” on Monday.
Microsoft President Brad Smith said Sunday that the attack used exploits stolen from the National Security Agency earlier this year.
“This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem,” Smith wrote on the Microsoft blog. “This is an emerging pattern in 2017. …
“This most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today — nation-state action and organized criminal action,” wrote Smith, who is also Microsoft’s chief legal officer.
…




![[Infographic] Manage Commercial Displays With Ease Across](https://loginby.com/itnews/wp-content/uploads/2026/02/1770220527_Infographic-Manage-Commercial-Displays-With-Ease-Across-100x75.jpg)
