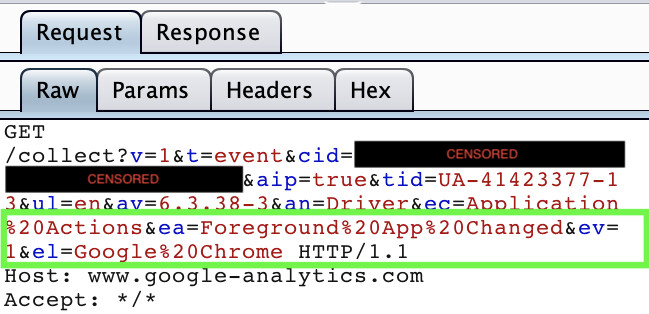
Heaton used Wireshark to first detect that his Wacom’s driver is sending knowledge packets to Google Analytics by monitoring its DNS lookups. The payload of knowledge despatched to the analytics web site was encrypted by TLS. He then arrange an inside proxy utilizing Burp Suite that satisfied the Wacom driver that it’s sending knowledge over a safe connection, and intercepted its payload. It was then found that Wacom driver tracks each utility its customers open (and never simply functions of curiosity to the corporate). The firm’s EULA do not search even implicit consent to gather this knowledge, and it presents a giant privateness problem. Heaton argues that what if this might be utilized by Wacom staff to, say, uncover that Valve software program is engaged on “Half Life 3,” by querying its knowledge heap for executables that sound like “Half Life 3”? Find a captivating technical run down of Heaton’s discovery on his weblog.