December 19, 2016 is a big day for Tor (The Onion Router) users as the Tor Project released the new Tor 0.2.9 stable series of the client/server implementation for enabling anonymous communication.
After so many months of development, the new Tor 0.2.9 stable series of the free and open-source software that prevents people and organizations from learning your Internet browsing habits or current location is finally here. As expected, it’s a major release that includes lots of goodies, starting with support for a new shared- randomness protocol that promises to lay the groundwork for next-gen hidden services, which will be used on all current and future Tor anonymous networks.
“It includes support for a new shared-randomness protocol that will form the basis for next generation hidden services, includes a single-hop hidden service mode for optimizing .onion services that don’t actually want to be hidden, tries harder not to overload the directory authorities with excessive downloads, and supports a better protocol versioning scheme for improved compatibility with other implementations of the Tor protocol,” reads the announcement.
OpenSSL 1.0.1 and libevent 2.0.10 are now required
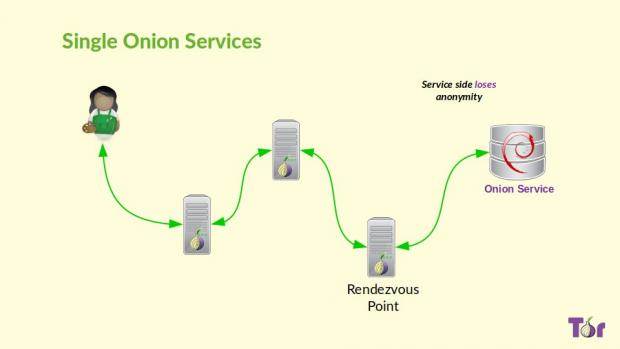
The list of new features included in Tor 0.2.9.8, which is the first stable release of the Tor 0.2.9 series, continues with support for OpenSSL 1.0.1 and libevent 2.0.10 libraries, or later versions. Previous builds of those libs are no longer supported and in no way recommended when building Tor. In the same manner, clients, relays, and authorities now require ntor keys in all descriptors for all circuits, hops, as well as other roles. There’s also support for single onion service, and it looks like ntor handshakes are now mandatory.
Additionally, Tor 0.2.9 is capable of preemptively closing connections of lower priority when detecting that it runs out of sockets, and there’s experimental support for the HiddenServiceNonAnonymousMode and HiddenServiceSingleHopMode options were implemented. To avoid epistemic attacks, the TAP key supplied by the protocol is now used for hidden service client-to-intro-point and service-to-rendezvous- point circuits. The full changelog is attached below, and you can download Tor 0.2.9.8 right now.