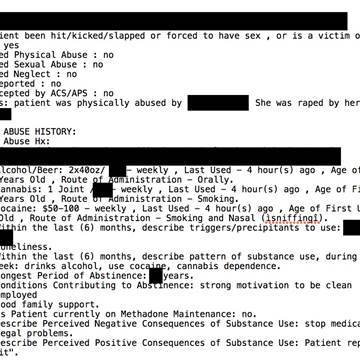
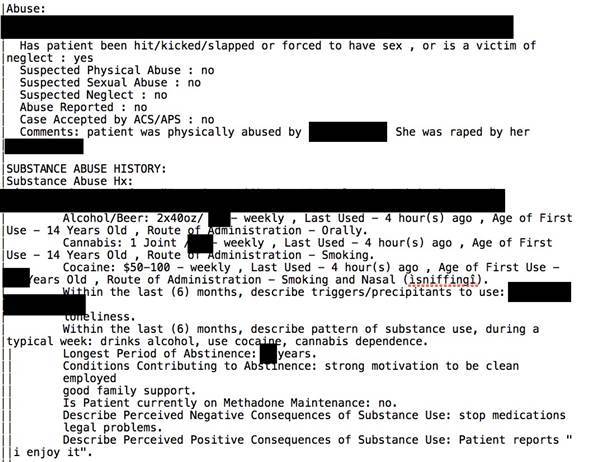
Medical records of at least 7,000 people compromised in a data breach involving Bronx Lebanon Hospital Center in New York disclosed patients’ mental health and medical diagnoses, HIV statuses and sexual assault and domestic violence reports, according to records reviewed by NBC News.
Other information in the compromised records, which online security experts said spanned 2014 to 2017, included names, home addresses, addiction histories and religious affiliations.

Bob Diachenko, a security researcher with MacKeeper Security Research Center, told NBC News on Tuesday the leak was caused by a misconfigured Rsync backup server hosted by iHealth, a Louisville, Kentucky-based company that offers records management technology.
It’s unclear how long the records were exposed, but “if you visited BLHC during that period of time, your patient history was probably there,” Diachenko said.
The type of medical records exposed in the data breach are protected under the Health Insurance Portability and Accountability Act (HIPAA). In its summary of the HIPAA security rule, the Department of Health and Human Services noted that “the rise in the adoption rate of these technologies [electronic health records] increases the potential security risks.”
Diachenko’s team discovered the leak in early May during a routine sweep of the internet using Shodan, a search engine for networked devices from webcams to databases and industrial systems.
“Just one ‘addiction intake’ file that researchers reviewed painted a full picture of the patient’s drug use, medical history and suicidal thoughts and many other data points that the average person would never even consider,” Diachenko said.

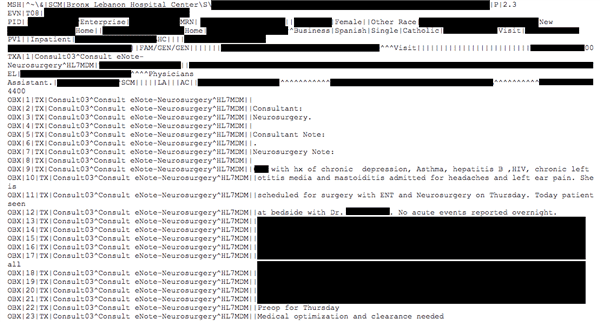
Bronx-Lebanon Hospital Center confirmed the breach to NBC News.
“iHealth Solutions, Inc. (iHealth) confirmed to Bronx-Lebanon Hospital Center that an iHealth server containing hospital data was the target of an unauthorized hack by a third party. The hospital and its vendor, iHealth, took immediate steps to protect the data,” the hospital said in a statement via email.
“The hospital is cooperating fully with law enforcement agencies,” it said.
iHealth told NBC News on Tuesday night that only one person had unapproved access to the data. It said it immediately took steps to identify and remediate the issue, including an internal review.
“While iHealth continues to work with a leading IT security firm to validate its analysis, at this time, iHealth believes that the issue has been contained,” the company said. “iHealth has no indication that any data has been used inappropriately.”
Leaks from Rsync servers, which transfer and synchronize files across computer systems, are common; in Feburary, NBC News reported that misconfigured protocols at PIP Printing exposed thousands of documents, including the medical records of National Football League players and confidential filings in a sexual harassment lawsuit at the company that publishes Hustler magazine.
In a blog post Tuesday, data security journalist Dissent Doe wrote that she was “tired of reporting” on leaks blamed on a simple protocol error in a server’s firewall.
“How many more nude photos of patients or ultrasound images will be exposed,” Doe asked, “because of misconfigured Rsync backups?”
“It’s almost as if no one is listening to any of the researchers begging entities to secure their data,” Doe added, pointing to the arrest of Justin Shafer, a security researcher who was raided by the FBI after he wrote a blog post about exposed patient data leaked by a dental software company.
The difference between white hat security researchers and malicious hackers is stark. While malicious hackers could access leaked data with the intentto steal or blackmail, researchers like Diachenko scan for leaks to inform companies so they can repair them — and protect consumer and patient privacy.
Diachenko had words of advice for techies looking to ensure maximum protection for their sensitive data storage.
“It’s important to follow the golden rules of ‘cyber hygiene’: you need to continuously check (ping) your ‘internal’ IP from the external environment,” Diachenko said. “And, of course, don’t forget to put a password on a backup device.”