An online security breach at a national printing chain leaked thousands of sensitive documents — from labor filings involving NFL players to lawsuits against Hollywood studios to personal immigration-related papers — raising the possibility that private information could end up in the wrong hands.
The leak at PIP printing, which has more than 400 locations in 13 countries, went on for four months before it was repaired Tuesday, cybersecurity experts involved in investigating the breach told NBC News. But there’s no evidence that any hackers may have stumbled upon the files to use them for malicious purposes, they add.
The documents, which NBC News examined, ranges from emails revealing credit card and social security numbers to legal filings such as depositions, subpoenas and labor lawsuits. Extensive medical records belonging to high-profile athletes were also at risk.
PIP owner Michael Bluestein told NBC News that the breach appeared to stem from a third-party IT firm that accidentally misconfigured the backup protocols — essentially leaving a “back door” open in the system.
“After discovering the breach, we acted quickly to lock down access to our database,” Bluestein said. “We immediately strengthened our security controls. We changed all passwords, took offline all computers that may have been affected and brought in forensic IT experts.”
Bluestein added that stronger-than-normal protections are being employed to further lock down the PIP system: “New firewalls are being installed. We are even going above the recommended security measures by also creating closed VPNs (virtual private networks) for our backup files,” he said.
Bob Diachenko, whose firm Mackeeper Security Research Center investigated the breach, said it was first discovered in October.
The data breach potentially allowed access to sensitive labor filings on behalf of NFL players, such as disability claims with extensive HIPAA-protected medical records attached.


The NFL and the National Football League Players Association, a union for the players, both declined to comment on the private records of their athletes being exposed in the security breach.
One particularly salacious set of documents released in the leak pertained to a lawsuit filed against Hustler by a former male employee who claimed adult magazine publisher Larry Flynt’s daughter sexually harassed him.
The suit was covered in the press after it was filed — but according to the leaked internal company documents, Hustler officially terminated the employee for failing to detect a “theft ring” at the Hustler Hollywood stores he oversaw as a district manager.
Hundreds of internal Hustler company documents were also leaked, including detailed sales records, profit and loss statements, company goals, and internal investigations relating to theft and human resources.
Hustler’s parent company, LFP Publishing, did not respond to multiple requests for comment.
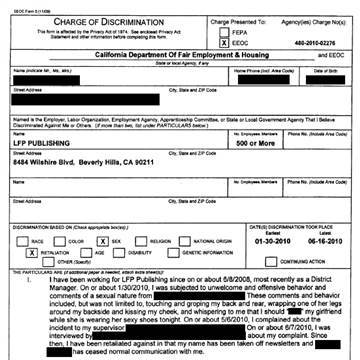
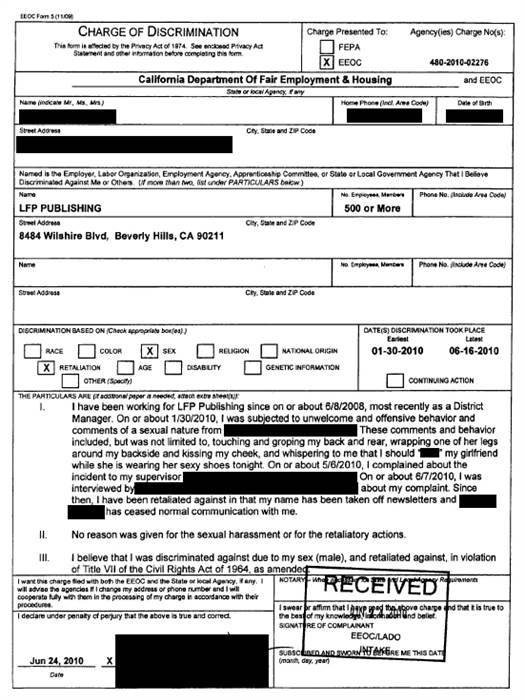
In addition, a number of California-based law firms were affected in the breach, with papers related to immigration and lawsuits against powerhouse Hollywood studios among those leaked.
Mackeeper said the PIP breach can be attributed to a misconfigured “rsync” backup system — such vulnerabilities occur all-too frequently.
Over the past year, Mackeeper’s security research team has discovered a number of leaks occurring through misconfigured rsync protocols including — but hardly limited to — footage of an inmate’s death in a California jail, an exposed system at a North Carolina Emergency Medical Services department, and 11 gigabytes of sensitive data regarding Pentagon employees with the Special Operations Command.
Those discoveries weren’t even listed in a year-end tally published by the blog IT Governance, which estimated at least 3.1 billion records leaked in 2016 alone through various breaches and hacking attacks.
Mackeeper’s team — comprised of Diachenko, Chris Vickery and Jeremiah Fowler — spends about three hours each day scanning the internet for security faults using Shodan, a search engine that allows users to examine all internet-connected devices.
Diachenko said Mackeeper made multiple attempts to notify PIP’s parent company, Franchise Services, without initial success.
“We try to identify the owner of the database/device and immediately report it to them,” Diachenko said of Mackeeper’s “responsible disclosure” policy. “Sometimes it takes weeks, sometimes — just a couple of minutes. Sometimes we got threats instead of a ‘thank you,’ so it is a challenging task.”
Initial suspicion aimed at security researchers usually comes from companies who often don’t understand that their data breach occurs within the system, not through hacking or any kind of outside attack.
Luckily, experts say, not many people have the computer literacy needed to stumble across such security faults — and so-called “white hats” like Diachenko hope that by routinely searching for them, they’ll get to the leaks before data thieves do.
“Accessing rsync is almost as simple as accessing an ftp,” Diachenko said in an email. “This is not an average user skill, but I would estimate that 1 of 10 users can do it. Thankfully, this number is not big enough, so we can responsibly disclose those breaches before they are affected by malicious actors.”







