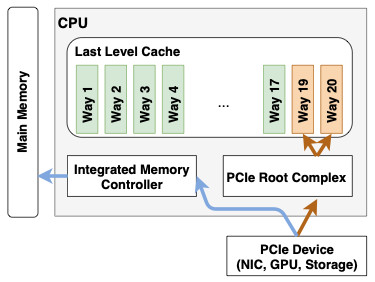
DDIO, or Direct Data I/O, is an Intel-exclusive efficiency enhancement that enables NICs to instantly entry a processor’s L3 cache, fully bypassing the a server’s RAM, to extend NIC efficiency and decrease latencies. Cybersecurity researchers from the Vrije Universiteit Amsterdam and ETH Zurich, in a analysis paper revealed on Tuesday, have found a important vulnerability with DDIO that enables compromised servers in a community to steal knowledge from each different machine on its native community. This embrace the flexibility to acquire keystrokes and different delicate knowledge flowing by means of the reminiscence of weak servers. This impact is compounded in knowledge facilities that haven’t simply DDIO, but in addition RDMA (distant direct reminiscence entry) enabled, during which a single server can compromise a whole community. RDMA is a key ingredient in shoring up efficiency in HPCs and supercomputing environments. Intel in its preliminary response requested clients to disable DDIO and RDMA on machines with entry to untrusted networks, whereas it really works on patches.
The NetCAT vulnerability spells large hassle for webhosting suppliers. If a hacker leases a server in a data-center with RDMA and DDIO enabled, they will compromise different clients’ servers and steal their knowledge. “While NetCAT is powerful even with only minimal assumptions, we believe that we have merely scratched the surface of possibilities for network-based cache attacks, and we expect similar attacks based on NetCAT in the future,” the paper reads. We hope that our efforts warning processor distributors in opposition to exposing microarchitectural parts to peripherals with no thorough safety design to stop abuse.” The staff additionally revealed a video briefing the character of NetCAT. AMD EPYC processors do not assist DDIO.
The video detailing NetCAT follows.
Source hyperlink
Post Views:
418