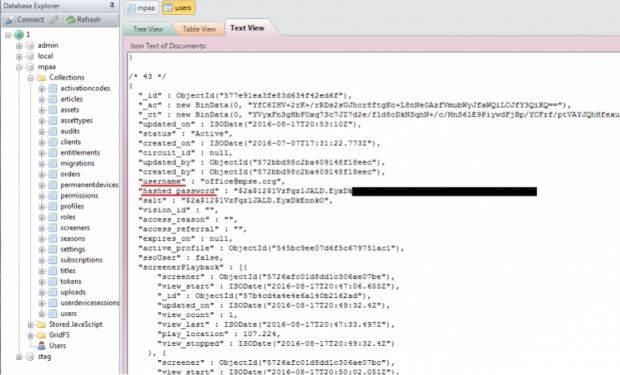
For an unknown period of time, the database associated with the website where members of the US film industry go to preview unreleased Hollywood movies (called screeners) had been left exposed to the Internet without an administrative password.
Anyone that knew where to look would have been able to access the database and download its content, which among various details regarding available screeners, also contained passwords for the accounts used to log into the site and watch the unreleased movies.
The good news for Hollywood studios is that the passwords were hashed with the bcrypt algorithm and an additional salt (random characters). Cracking these passwords would take years of computational operations.
Accounts for movie studio employees were included in the database
According to Chris Vickery, security researcher for MacKeeper and the person who discovered the exposed server, the database contained accounts for users that registered with emails with the following domains: @paramount.com, @disney.com, @warnerbros.com, @fox.com, and @spe.sony.com.
Since the attacker had full administrative access to these accounts, he wouldn’t have needed to crack the passwords, but simply guess the hashing algorithm and replace a password for an existing account, or create a new profile for himself.
Immediately after discovering the database Vickery contacted Vision Media Management (VMM), the company which the MPAA (Motion Picture Association of America) hired to create the website, as an alternative to sending DVD screeners via post to its members.
This website, located at awards-screeners.com, is used by MPAA members to view and vote for movies contending every year for the Oscars.

Vickery notes that after contacting the company, he was pleasantly surprised to discover that VMM took the data breach very seriously and was immediately connected to VMM’s lead internal counsel, and then to the company’s CTO.
VMM secures database on the same day
VMM took immediate steps to shut down access to the database, while Vickery was put in the awkward position of explaining to the rest of the counsel that he wasn’t trying to extort them.
Things got carried away after VMM hired a famous lawyer, expert in data breach law, who tried to intimidate Vickery accusing him of improperly downloading a copy of the database, which Vickery always does as proof in case companies deny any security breaches.
Vickery quickly put the lawyer in her place, reminding her of his long history in exposing unsecured databases.
“I have cooperated with and contributed to data breach-related investigations conducted by the FTC, FBI, US Navy, HHS/OCR, US Secret Service, and other similar entities,” Vickery replied in an email. “Not a single regulatory or government agency I have interacted with has even suggested that what I do, downloading publicly published information, is improper.”
In later email exchanges, VMM told Vickery that most of the data he downloaded was actually test data. Vickery says he found information on 1,200 user accounts, but VMM informed him that only 160 of those records were from real users.
Vickery also sifted through the rest of the data dump and he discovered links to three Amazon S3 servers, also exposed to the Internet without authentication, where the company stored details about various developer tools and API integrations. Vickery says that VMM didn’t yet reply to his last report.