![]() Microsoft
Microsoft ![]() is taking a bow for saving the public from potential malware
is taking a bow for saving the public from potential malware ![]() infection through counterfeit Windows
infection through counterfeit Windows ![]() software
software ![]() by taking over a domain that hosted as many as 70,000 malicious subdomains.
by taking over a domain that hosted as many as 70,000 malicious subdomains.
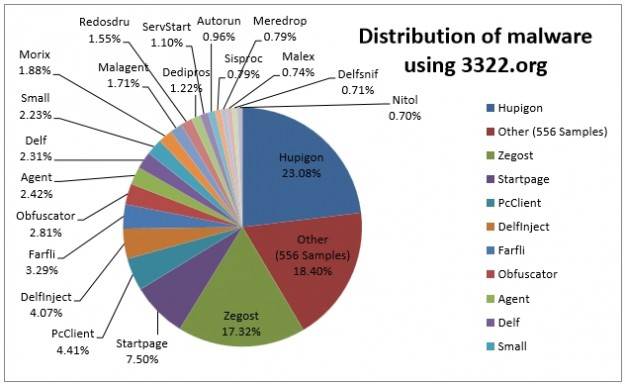
The digital ![]() drama unfolded earlier this week when the cyber-sleuths at the tech giant’s Digital Crimes Unit acted on research that showed that crooks were using fake software to infect computers with malware connecting to the Nitol botnet. The botnet activity via the domain 3322.org, dated back to 2008.
drama unfolded earlier this week when the cyber-sleuths at the tech giant’s Digital Crimes Unit acted on research that showed that crooks were using fake software to infect computers with malware connecting to the Nitol botnet. The botnet activity via the domain 3322.org, dated back to 2008.
A botnet is a system of computers that has been compromised by hackers.
‘Eyes and Ears’ for Hackers
“We found malware capable of remotely turning on an infected computer ![]() ‘s microphone and video camera, potentially giving a cybercriminal eyes and ears into a victim’s home or business,” wrote Richard Domingues Boscovich
, assistant general counsel of Microsoft’s Digital Crimes Unit, on Microsoft’s official blog Thursday. “Additionally, we found malware that records a person’s every keystroke, allowing cybercriminals to steal a victim’s personal information.”
‘s microphone and video camera, potentially giving a cybercriminal eyes and ears into a victim’s home or business,” wrote Richard Domingues Boscovich
, assistant general counsel of Microsoft’s Digital Crimes Unit, on Microsoft’s official blog Thursday. “Additionally, we found malware that records a person’s every keystroke, allowing cybercriminals to steal a victim’s personal information.”
As part of its Project MARS (Microsoft Active Response for Security) program, Redmond, Wash.-based Microsoft filed suit in the U.S. District Court for the Eastern District of Virginia, seeking a temporary restraining order against an individual named Peng Yong, his company and other unnamed individuals, which was granted on Monday. Yong denies any wrongdoing.
That order allowed Microsoft to take control of the 3322.org domain through a new domain system that allows the company to block Nitol and nearly 70,000 other malicious sites while keeping traffic to legitimate sites flowing normally.
“In an operation like this, you are trying to take the servers that are botted offline once you identify them,” explained technology consultant Rob Enderle of the Enderle Group. “Once you identify the IP address, you isolate the machines so they can’t talk to anyone else, which effectively shuts them down. It’s like what you would do with a person who has a communicable disease.”
Good Hunting
He added that in Europe, Microsoft has disrupted malicious servers by having them physically shut down by law enforcement agents, but domestically is more likely to work to have them disconnected from other networks.
In granting the restraining order, the District Court said that “there is good cause to believe that Defendants have engaged in intentionally and/or negligent activity using the 3322.org domain that is maintained by the top level domain registry, the Public Interest Registry (“PIR”), located in Reston, Virginia.”
Boscovich noted that it’s the second botnet disruption carried out by the Digital Crimes Unit in the last six months.
In July, the unit announced that it had identified two defendants behind the Zeus botnet, which is believed to be responsible for a half-billion dollars in online fraud and identity theft. Those individuals were already serving time in the United Kingdom for Zeus-related malware charges, Boscovich said.
 iView 7-Inch Android Netbook
iView 7-Inch Android NetbookFeatures: 7″ Digital LCD Screen, VGA 800 x 480 pixel. Android 2.2 OS. 256MB RAM. 4 GB Nand Flash. WiFi b/g Ethernet port. Google W…
 Apple iBook G4, 1.33 GHz, 768MB RAM, 40 GB Hard Drive, Internal Combo Drive, 56k Modem
Apple iBook G4, 1.33 GHz, 768MB RAM, 40 GB Hard Drive, Internal Combo Drive, 56k ModemRAM of 768MB ; 40 GB internal drive internal Combo Drive ; internal 56k modem Airport Extreme and Bluetooth installed ; 12.1″ TFT …