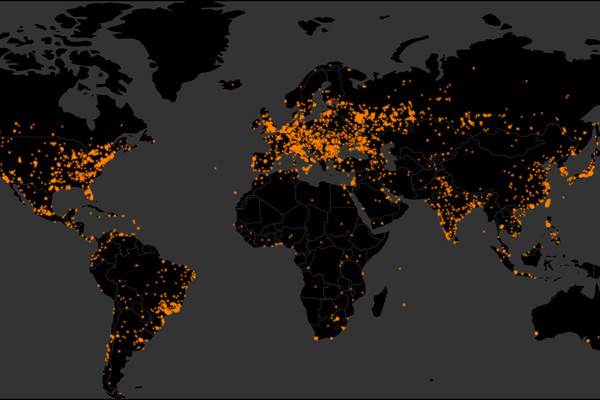
Windows may be the operating system that’s affected by the WannaCrypt ransomware, but Microsoft isn’t taking all of the blame. Brad Smith, the company’s chief legal officer, has pointed a finger at the US government.
The NSA knew about the exploit in question and instead of reporting it to Microsoft, it held on to the security hole in order to create hacking tools. The Shadow Brokers then leaked data from the NSA that revealed the vulnerability, enabling WannaCrypt’s existence.
This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem. This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today – nation-state action and organized criminal action, – Smith
According to Smith, this situation should act as a “wake-up call” for governments. Microsoft believes they should stop gathering exploits in this manner due to the potential for similar situations to occur.
Microsoft isn’t placing all of the blame on the government though. It admits to being partly responsible, alongside IT administrators and users who didn’t update their systems.