The fervor of cryptocoin mining has consumed a big a part of the semiconductor business of late. The calls for for top efficiency silicon to mine these digital belongings with worth is one consider a world scarcity of obtainable components for computer systems, cars, protection, analysis, and different industries. One constant aspect to cryptocoin mining during the last decade is the prevalence of hijacked machines and units by means of malware, generally often known as botnets. Previously these armies of machines had been co-opted to carry out bandwidth assaults towards varied targets, however they’ve additionally been used for his or her compute sources – mining cash which have worth for those who management the botnet. This week Intel and Microsoft are asserting an extra layer of safety towards these kinds of assaults.
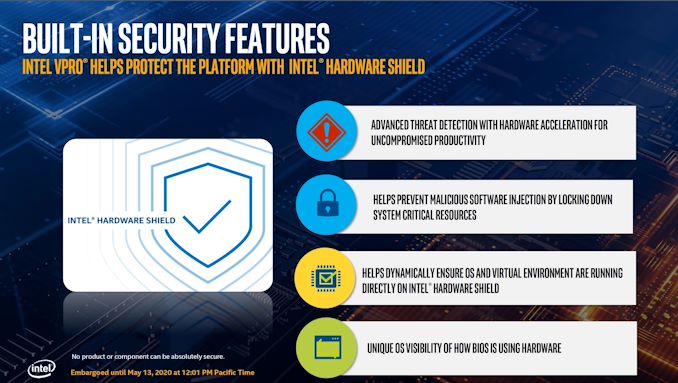
Commercial machines operating Microsoft Windows, and managed by means of Microsoft Defender for Endpoint, can now be protected towards CPU cryptocoin mining by means of an AI-backed safety mechanism. The safety layer requires an Intel processor with Intel’s Hardware Shield (a vPro know-how) and Threat Detection Technology enabled, which was launched in 2018, and makes use of a mixture of instruments (similar to CPU and GPU) to research the code being processed at a low degree.
By performing constant heuristic evaluation by means of the CPU efficiency monitoring unit at a low degree, the system can detect whether it is mining with out the proprietor’s consent. This may be detected both by means of a compromised hypervisor, digital machine, or within the OS instantly hidden as a separate course of. If a risk is detected, an Endpoint detection and response answer is carried out to neutralize the mining utility, or quarantine it, and forestall the code from spreading throughout a community or fleet of managed techniques.
Intel lists that over a billion CPUs can allow its Threat Detection Technology, from its 6th Generation processors onwards – Microsoft additionally highlights that Defender for Endpoint with TDT is supported on these techniques. However each firms disguise the very fact in a footnote that the particular Cryptomining detection implementation is barely attainable on 10th Generation and newer platforms. It can also be value noting that this requires Intel’s Hardware Shield, which implies vPro can also be a requirement. So whereas there are a possible billion CPUs with some degree of TDT available in the market, this explicit answer is barely relevant to Windows primarily based vPro machines managed at a company degree. Still vital, however not as large because the one billion quantity that Intel is selling. Intel doesn’t listing TDT as a function on its most important processor archive, ark.intel.com, both. It must also be famous that Intel TDT with reminiscence scanning does eat built-in graphics sources to observe the system – whereas this offers extra energy for CPU duties, it undoubtedly raises the facility consumption of techniques when idle, which for cellular techniques will scale back battery life. This is an final tradeoff for safety vs battery life.
Microsoft highlights that the ML-based know-how used as a part of TDT and Endpoint for Defender is a relative tip of the iceberg, offering a automobile for extra complete safety towards ransomware or side-channel assaults in future. These require pre-trained ML algorithms which Microsoft is at present engaged on and can roll-out as a part of its Endpoint for Defender answer.
Despite the truth that low-end CPU cryptomining isn’t definitely worth the effort for informal customers, for those who management botnets of 1000’s of machines, it finally ends up incomes them a number of further bucks utilizing electrical energy they don’t seem to be paying for, even in small IoT deployments similar to safety cameras. However there’s a new class of cryptocurrency mining which is much less compute reliant, and as a substitute is…