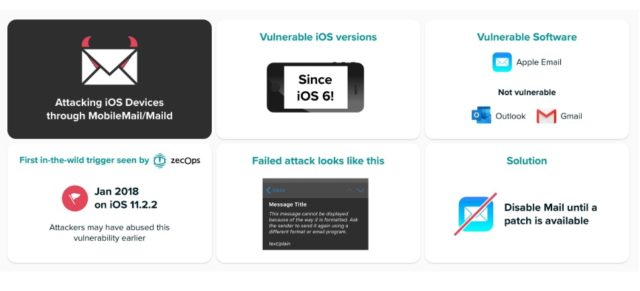
Two new critical safety vulnerabilities in Apple iOS working system have been revealed right now. These vulnerabilities permit attackers to achieve entry to an iOS gadget with none consumer motion. Generally, when a consumer clicks some hyperlink or installs some software, the vulnerability will likely be exploited. But on this case, the attacker can simply ship emails that devour a big quantity of reminiscence and get distant code execution capabilities within the gadget. According to safety agency Zecops, attackers are already utilizing these vulnerabilities within the wild focusing on the next:
Individuals from a Fortune 500 group in North AmericaAn govt from a service in JapanA VIP from GermanyMSSPs from Saudi Arabia and IsraelA Journalist in EuropeSuspected: An govt from a Swiss enterprise
All gadgets operating iOS 6 and above are affected by these safety flaws. In the current iOS variations, the assault could be carried out by the beneath methods:
Attack on iOS 13: Unassisted (/zero-click) assaults on iOS 13 when Mail software is opened within the backgroundAttack on iOS 12: The assault requires a click on on the e-mail. The assault will likely be triggered earlier than rendering the content material. The consumer received’t discover something anomalous within the e-mail itselfUnassisted assaults on iOS 12 could be triggered (aka zero click on) if the attacker controls the mail server
Apple is conscious of those safety flaws in iOS and will likely be releasing an replace quickly to repair these. If you need to forestall such assaults till Apple releases an replace, you could keep away from utilizing the Apple mail app. Instead, you need to use the Microsoft Outlook app or different related e-mail purchasers.
You can be taught extra about these vulnerabilities from the
Source hyperlink