Transitioning to microservices has many benefits for groups constructing massive functions, significantly those who should speed up the tempo of innovation, deployments, and time to market. Microservices additionally present know-how groups the chance to safe their functions and companies higher than they did with monolithic code bases.
Zero-trust safety offers these groups with a scalable option to make safety fool-proof whereas managing a rising variety of microservices and higher complexity. That’s proper. Although it appears counterintuitive at first, microservices enable us to safe our functions and all of their companies higher than we ever did with monolithic code bases. Failure to grab that chance will end in non-secure, exploitable, and non-compliant architectures which can be solely going to develop into tougher to safe sooner or later.
Let’s perceive why we’d like zero-trust safety in microservices. We may even evaluate a real-world zero-trust safety instance by leveraging the Cloud Native Computing Foundation’s Kuma undertaking, a common service mesh constructed on prime of the Envoy proxy.
Security earlier than microservices
In a monolithic software, each useful resource that we create might be accessed indiscriminately from each different useful resource by way of perform calls as a result of they’re all a part of the identical code base. Typically, sources are going to be encapsulated into objects (if we use OOP) that may expose initializers and features that we will invoke to work together with them and alter their state.
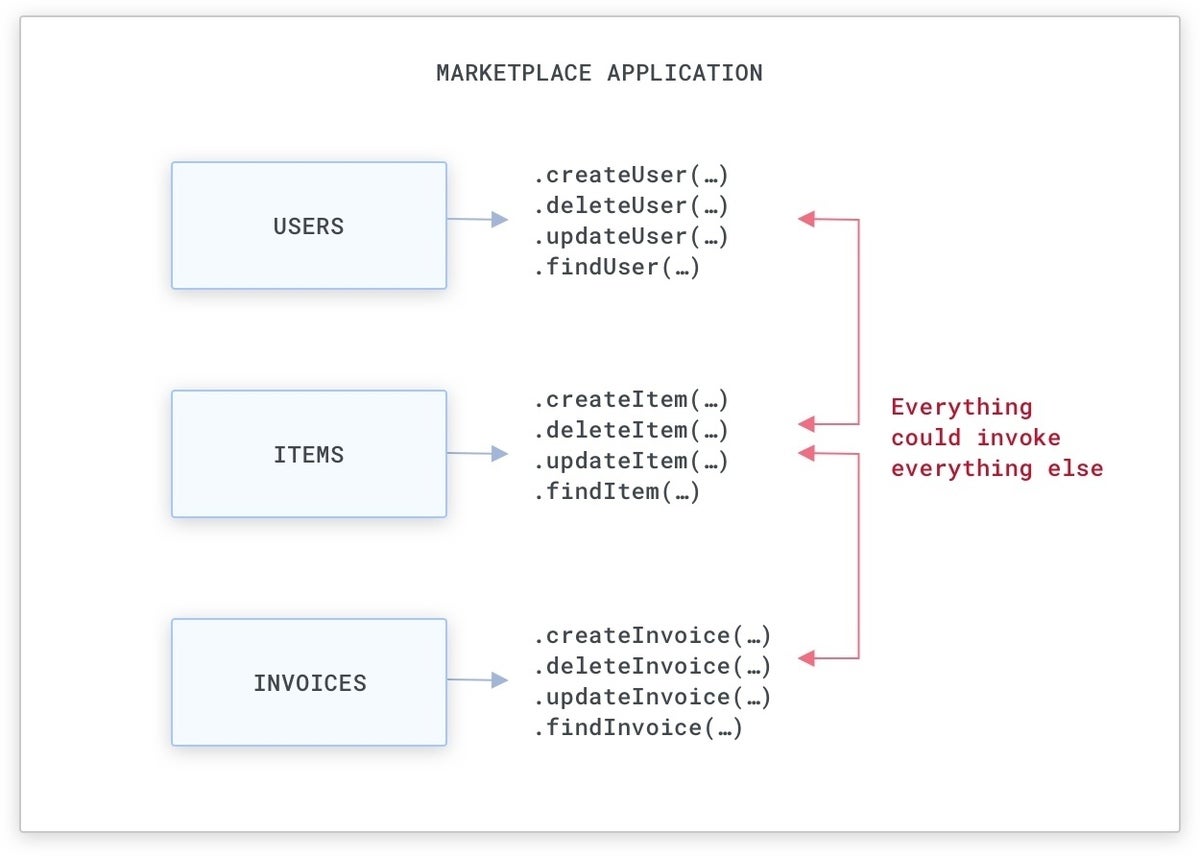
For instance, if we’re constructing a market software (like Amazon.com), there shall be sources that determine customers and the gadgets on the market, and that generate invoices when gadgets are bought:
A easy market monolithic software.
Typically, this implies we can have objects that we will use to both create, delete, or replace these sources by way of perform calls that can be utilized from wherever within the monolithic code base. While there are methods to cut back entry to sure objects and features (i.e., with public, personal, and guarded access-level modifiers and package-level visibility), normally these practices should not strictly enforced by groups, and our safety shouldn’t rely on them.
 Kong
KongA monolithic code base is simple to use, as a result of sources might be doubtlessly accessed by wherever within the code base.
Security with microservices
With microservices, as a substitute of getting each useful resource in the identical code base, we can have…