Our lives have been remodeled by the COVID pandemic. We have modified the best way we work remotely and are unlikely to be again to the workplace fully; a hybrid office is right here to remain.
According to analysis launched by S&P Global in June 2020, 80% of firms surveyed had applied or expanded common work-from-home insurance policies in response to the disaster, and 67% anticipate these to stay in place both for the long run or completely. As extra individuals proceed to work remotely, the variety of connections will increase and so does the potential assault floor.
Analysis of the menace panorama, and most lately the SolarWinds breach, discovered that hackers are sometimes capable of achieve broad techniques entry. In many circumstances, the hackers transfer by way of networks unfettered to arrange again doorways and administrator accounts. With workers now connecting in giant numbers, they’re making a hacker’s playground, with new, susceptible endpoints and entry factors being uncovered. New frameworks and instruments are required to handle these threats.
Defining SASE and Zero Trust
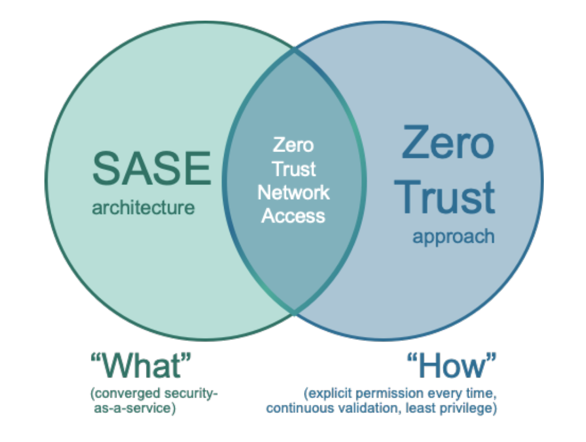
Secure Access Service Edge (SASE), a phase coined by Gartner Research, and Zero Trust, created by Forrester Research, are two such frameworks that may assist shield our workers.
Zero Trust as an idea has been round for a decade at the least. In its easiest type it’s: Don’t belief the issues you don’t want to belief. For the issues you need to belief, belief however confirm continuously. Today there are various remoted Zero Trust initiatives centered on networks, customers, units or servers.
The SASE mannequin combines networking and community safety providers, cloud entry safety dealer (CASB), firewall as a service (FWaaS), knowledge loss safety (DLP) and extra, right into a single complete, built-in resolution that helps all site visitors, functions and customers.
It’s all about defensive safety technique
Both SASE and Zero Trust help a brand new strategy: a defensive safety technique on the edge. The mannequin requires an inspection to happen on the service edge. “The model would be to understand the identity of the employee, the student, or contractor based on their access identity. But at no point are they on the network, and you assign trust based on where they are in that network topology,” Patrick Sullivan, CTO of Akamai and an skilled on safety, stated.
Such a proxy would permit entry to internet providers irrespective of the place they’re hosted—and even to providers hosted in native company networks.
Such an strategy helps conceal inner internet functions and keep away from posing them to the web, offering safe entry through proxy. This eliminates the usage of a VPN as a result of internet functions could be accessed from wherever through proxy in a safe manner making use of Zero Trust alone. The flexibility of deploying safety inspection on the edge signifies that, no matter shifts within the location of computing, safety inspection could be carried out at a neighborhood edge node.
Furthermore, since multi-cloud is the predominant structure, deploying safety at a homogeneous edge makes extra sense than attempting to engineer constant controls utilizing heterogeneous capabilities accessible at numerous cloud safety suppliers (CSPs).
Enterprises must be intentional about this
Analysts agree that an efficient safety implementation takes time, dedication and cultural change. The following factors must be evaluated and thought of:
- Multiple layers of safety
- Enterprise-level safety round any kind of connection
- Simplified deployment
- Scalability
- Improved community efficiency
- Lower operational overhead
The key to implementing safety frameworks resembling SASE and Zero Trust is to scale back complexity whereas additionally rising visibility and ease of administration. It is…