Effectively battling threats requires actionable intelligence, one thing many organizations lack right now. Typically, compromises or threats are solely found someday after an incident happens, turning what ought to have been a protection into incident response. That lack of fast discovery probably creates darkish areas in IT, the place lateral assaults, knowledge exfiltration and different compromises can go on for days, weeks and even months.
What’s extra, the harm that happens between an lively risk and its discovery may be business-ending, particularly for small- and medium-size enterprises. According to IBM, the typical price of an information breach in 2020 was $3.86 million, and the typical lifecycle of a breach was 280 days from identification to containment. Simply put, the excessive prices of undetected compromises and breaches are issues that almost all organizations can not face up to.
Miami, Florida-based Lumu goals to place an finish to that lack of risk discovery with an modern platform that always screens IT infrastructures for compromises, permitting motion to be taken rapidly. Lumu’s mantra is certainly one of offering cybersecurity professionals with actionable details about compromises, whereas additionally figuring out the so-called darkish areas of IT to assist IT staffers harden their defenses.
A better have a look at Lumu
Lumu is a platform-based strategy for steady compromise evaluation that leverages metadata to establish confirmed compromise incidents. The platform makes use of a number of knowledge sources to grasp the conduct of enterprise networks, which in flip can be utilized as an evidence-based methodology to establish areas topic to threats and compromises. Meanwhile, it provides safety professionals distinctive insights into the extent of compromise skilled on the community.
Lumu is obtainable in three completely different flavors:
- Lumu Free is obtainable as a free service, and it has restricted capabilities. Lumu Free provides restricted visibility of confirmed IoCs (Indicator of Compromise), entry to the Lumu Portal, real-time DNS ingestion, steady compromise assessments of as many as 10 gateways.
- Lumu OnDemand provides further options, comparable to ad-hoc compromise evaluation, guide ingestion of quite a few metadata sources and actionable insights, together with cybersecurity posture suggestions and knowledge on how one can mitigate detected compromises.
- Lumu Insights, the corporate’s premier service, provides further options that ought to show very precious to any crew liable for attempting to find threats and coping with compromises. That service provides detailed visibility into IoCs, in addition to community site visitors groupings. Network metadata ingestion turns into automated and is carried out in real-time. Other options embody an infinite digital equipment knowledge collector, assault sample recognition, in depth reporting, and plenty of different novel options.
Hands-on with Lumu Insights
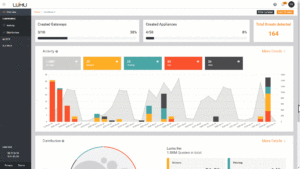
Lumu Insights is the top-tier product provided by the corporate and as such provides probably the most in depth function set. Lumu Insights is deployed utilizing a digital equipment, which is ready to acquire knowledge from the community’s prolonged perimeter. The firm additionally provides brokers for many working programs, which in flip offers further insights into endpoints–together with these which are distant.
[To see a bigger view of this picture, right-click on it and choose “View Image.”]
Lumu Insights is ready to collect metadata from the native community in addition to the cloud, and in addition from distant endpoints. The Lumu digital equipment runs on current hypervisors and is ready to collect DNS queries as they traverse the community, whereas additionally amassing netflow info and log knowledge. The platform collects a variety of community metadata, together with DNS, netflows, proxy and…




![[CES 2026] An Entertainment Companion for Every Moment Seen](https://loginby.com/itnews/wp-content/uploads/2026/01/1768923629_CES-2026-An-Entertainment-Companion-for-Every-Moment-Seen-100x75.jpg)
