How HTML5 Ping Is Used in DDoS Attacks
A brand new sort of distributed denial-of-service (DDoS) assault is abusing a typical HTML5 attribute to overwhelm focused victims.
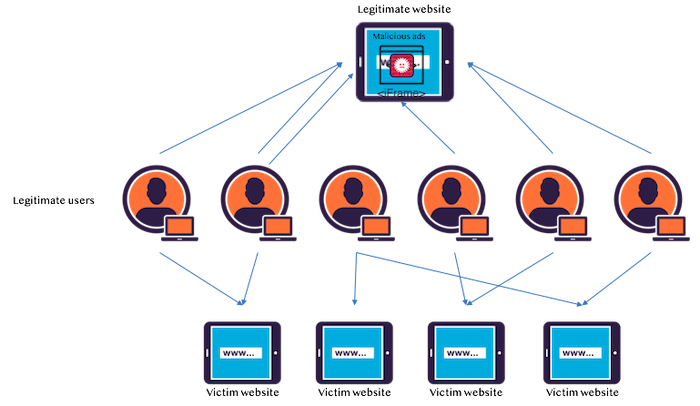
Security agency Imperva reported on April 11 that it has found a marketing campaign the place hackers abused the <a> tag ping HTML5 attribute in a DDoS assault that generated 70 million requests in 4 hours. The ping attribute is meant for use by web sites as a mechanism to inform an internet site if a person follows a given hyperlink on a web page. Typically, a ping is a single motion, however Imperva found that hackers have discovered a solution to amplify the ping right into a extra persistent knowledge circulation, triggering the DDoS assault.
“The attacker, probably using social engineering, forced users to visit a website that contained malicious JavaScript,” Vitaly Simonovich, safety researcher at Imperva, informed eWEEK. “This script generated links with the target site in the ‘ping’ attribute and clicked it without personal involvement of the user. Auto-generated clicks reflected as ping back to the victim, continuously, the entire time the user stayed on the webpage.”
Further studying Cyber-Security Incident Response Plans Lacking The Big Personal Hack That Almost Happened
Imperva’s evaluation of the assault defined that when the person clicks on the hyperlink, a POST request with the physique “ping” shall be despatched to the URLs specified within the attribute. It may also embody headers “Ping-From,” “Ping-To” and a “text/ping” content material sort.
“We observe DDoS attacks daily,” Simonovich mentioned. “We discovered this attack last month. However, when we looked back in our logs, we noticed that the first time the attack occurred on our network in December 2018, it was using the ping feature.”
The assault that Imperva discovered was ready make use of 4,000 person IPs, with a big share of them from China. The marketing campaign lasted 4 hours, with a peak of seven,500 requests per second (RPS), leading to greater than 70 million requests hitting the goal sufferer’s web site.How the Ping Attack Overwhelms a Server
A easy ping by itself just isn’t sufficient to disturb an internet server and, in truth, for fundamental availability internet servers are usually hit with ping requests. Ping requests are additionally low bandwidth and would not going be capable to represent a volumetric DDoS assault, which goals to overwhelm the accessible bandwidth of a goal server.
The DDoS assault found by Imperva, nonetheless, was not a fundamental ping and, based on Simonovich, may affect an internet software server in a pair methods:Targeting the net server utilizing excessive RPS, the server shall be pressured into processing the DDoS assault and never deal with professional visitors. Targeting the net software by discovering an injection level will trigger a excessive useful resource consumption. For instance, the login kind will trigger a question to the database.
“The attack is performed on the application layer aimed to clog server resources by processing several HTTP requests,” Simonovich defined. “As such, attack bandwidth is not the weakest resource in the chain, but CPU or memory of the server.”
He added that 7,500 RPS is much from essentially the most highly effective software DDoS assault, which may attain 100,000 RPS and extra, but it surely is sufficient to deny availability for a…