Effectively securing and defending Active Directory (AD) is an simple finest observe for companies immediately. Especially since some 90% of the world’s enterprise organizations are utilizing AD as their main technique for authentication and authorization.
AD’s huge market share has made it a main goal for attackers. In reality, cyberattacks on AD are so prevalent that Microsoft warns that some 95 million AD accounts are the goal of cyberattacks every single day.
AD homes a myriad of delicate info, corresponding to person account info, enterprise assets, ACLs, and so forth, making it a particularly enticing goal for cybercriminals. Simply put, if an attacker can exploit the data contained inside AD, they will do just about as they please with a corporation, together with stealing info, compromising functions, planting malicious software program, and even simply merely locking each person out of all functions.
It is a risk made much more dramatic by how AD is now used with Azure and Office 365, extending threats to the enterprise past simply on premise and into the cloud. Making due diligence much more important for cybersecurity professionals. Basic chores corresponding to common audits and defining insurance policies to guard AD should turn into the norm. However, these conventional finest practices have been confirmed to be inadequate, since organizations nonetheless fall prey to assaults on AD.
It is an issue finest outlined by a scarcity of visibility. In different phrases, cybersecurity execs lack full visibility into AD to detect assault surfaces, in addition to suspicious objects, or actions. Audits show solely helpful as a snapshot of AD’s standing at a given time, whereas exercise displays can’t usually lack the power to detect anomalous actions.
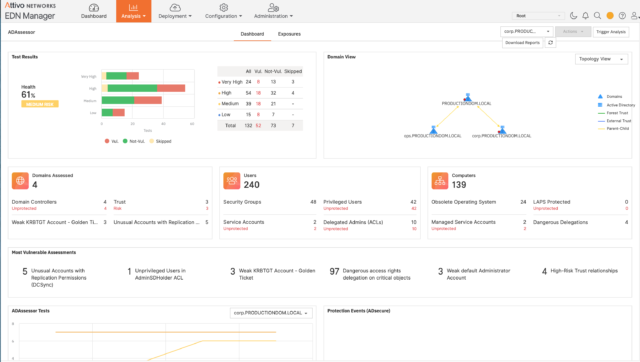
ADAssessor from Attivo Networks goals to deliver real-time visibility to AD fixing one of many largest challenges confronted by directors, the power to completely perceive what is going on behind the scenes in AD, uncover assault surfaces, and detect lively assaults.
A Closer Look at ADAssessor
ADAssessor is all about detection, visibility, and response for AD environments. In different phrases, the product is designed to deliver cyber hygiene to AD by constantly scanning AD for exposures, misconfigurations, and anomalous exercise in AD. What’s extra, ADAssessor gives real-time alerting for actions that signify that AD is underneath assault. Capabilities which might be akin to steady penetration testing for AD.
ADAssessor may be deployed on-premise or as a cloud hosted platform, both of which hyperlinks to Windows Domain Controllers to observe AD occasions, corresponding to change notifications, and detect misconfigurations, scan for potential assault vectors, or determine assaults in progress.
The product establishes the hyperlink between the cloud service and the area controller by putting in a software program shopper onto a site managed PC, which additionally acts as an endpoint that allows the product to detect endpoint primarily based assaults on the area controller.
ADAssessor makes use of a mix of detection and automation to drive response and alerting, which in flip acts on fast threats, whereas additionally informing directors of wanted actions.
Hands on with ADAssessor
ADAssessor connects to a site utilizing what might be finest described as a hybrid mannequin. Administrators might want to set up software program on an area PC endpoint, which acts as an ersatz connection between the area controller and the ADAssessor’s companies engine. There are a number of benefits to that technique of integration.
For instance, there isn’t a disruption in operations, which means that the area controller doesn’t should be shutdown or rebooted. What’s extra, the set up methodology helps preserve…