Chrome users should beware of a new hacking technique which prompts users to download a missing font only to trick them into installing malware on their systems.
According to cybersecurity firm NeoSmart Technologies, the trap was first noticed while browsing a WordPress website that had allegedly already been compromised. Given the latest issues with WordPress due to users failing to update to the latest security patch, this isn’t exactly a surprise.
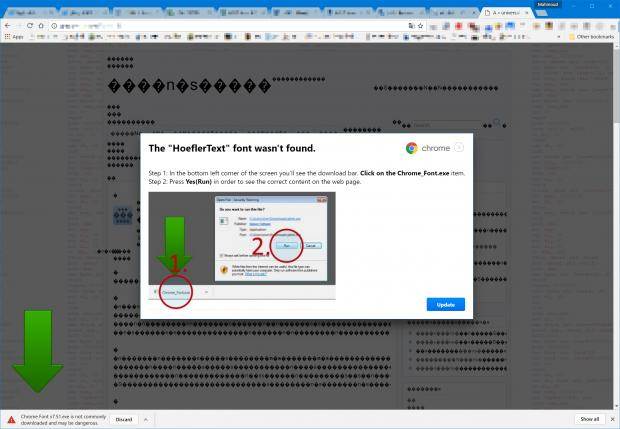
This particular attack was pretty well disguised. JavaScript was used to tamper with the text rendering on the site, causing it to look all jumbled. The script then prompted users to fix the problem by installing that one font they were missing to read the blog by updating the Chrome font pack. This makes for a rather credible ploy, especially since the dialog window that pops up urging users to update actually looks like it comes from Chrome. It even has the logo on the side and the right shade of blue on the “update” button.
There are some clues that things aren’t right, of course. On one hand, the dialog window insists that you’re using Chrome version 53 even if you aren’t. Then, clicking the “Update” button will proceed to download an executable file titled “Chrome Font v7.5.1.exe” which isn’t the same as the one the instruction image said it would download – “Chrome_Font.exe”.

It’s not flagged as malware
Chrome doesn’t flag the file as malware, but it does block it because the file isn’t downloaded too often, which is a common warning. The browser advises users to discard the file. Following a VirusTotal scan, only 9 out of 59 anti-virus scanners in the database accurately identify the file as malware, although VirusTotal has some issues with accurately presenting a list of antivirus programs that actually detect various malicious files, so the number may be higher than that.
There’s also the fact that you don’t need to update any Chrome font pack at any time because it already comes with everything you need.