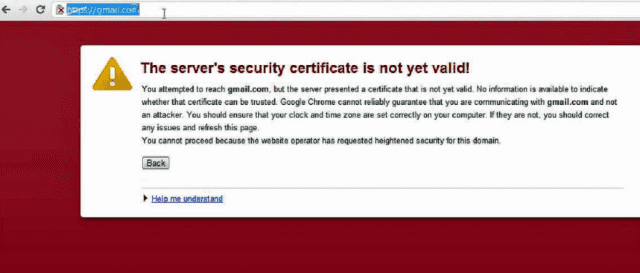
In the latest security lapse involving the Internet’s widely used encryption system, Google said unauthorized digital certificates have been issued for several of its domains and warned misissued credentials may be impersonating other unnamed sites as well.
The bogus transport layer security certificates are trusted by all major operating systems and browsers, although a fall-back mechanism known as public key pinning prevented the Chrome and Firefox browsers from accepting those that vouched for the authenticity of Google properties, Google security engineer Adam Langley wrote in a blog post published Monday. The certificates were issued by Egypt-based MCS Holdings, an intermediate certificate authority that operates under the China Internet Network Information Center (CNNIC). The Chinese domain registrar and certificate authority, in turn, is included in root stores for virtually all OSes and browsers.
The issuance of the unauthorized certificates represents a major breach of rules established by certificate authorities and browser makers. Under no conditions are CAs allowed to issue certificates for domains other than those legitimately held by the customer requesting the credential. In early 2012, critics blasted US-based CA Trustwave for doing much the same thing and Langley noted an example of a France-based CA that has also run afoul of the policy.
Read 5 remaining paragraphs | Comments
![]()