GoDaddy Removes 15,000 Subdomains That Were Scamming Users
Palo Alto Networks’ Unit 42 menace intelligence workforce introduced on April 25 that it labored along with GoDaddy to take down 15,000 subdomains that had been engaged in scam-related internet online affiliate marketing actions.
The impacted GoDaddy subdomains weren’t common clients doing unauthorized issues. Rather, the GoDaddy domains had been buyer accounts that had been breached after which modified to deal with the rip-off internet online affiliate marketing site visitors, which included weight-loss merchandise, amongst different items. According to Unit 42’s analysis, the GoDaddy subdomains had been doubtless breached by way of credential stuffing assaults. In a credential stuffing assault, passwords which were stolen in a single knowledge breach are then utilized by an attacker on different websites the place the victims had reused the identical passwords.
“These were GoDaddy accounts for regular customers,” Jeff White, principal menace researcher for Unit 42 at Palo Alto Networks, informed eWEEK. “Several hundred customers were impacted.”
Further studying Symantec Warns of Emerging Cryptojacking Campaign FBI Lists Business Email Compromise as Top Scam
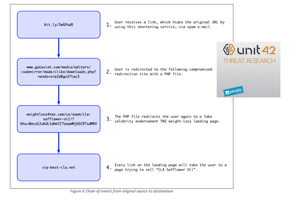
A subdomain is a variation on an web area identify, the place a prefix is added, which might then be directed to a particular IP handle location. For instance, safety.eweek.com is a subdomain that simply refers again to eWEEK.com. A GoDaddy help web page notes that customers can create as much as 100 subdomains per area identify.
White defined that with the compromised GoDaddy accounts, the attackers didn’t modify the CNAME (Canonical Name Record or Alias Record) with the Domain Name System (DNS) panel. DNS is the system that maps IP addresses to domains, and there are a number of sorts of DNS data which are used to assist direct site visitors. The “A” data are sometimes the first data which are used to map an IP handle to a reputation.
“These were A records that mapped to the IP for the GoDaddy redirector service, which would then subsequently forward a user to the affiliate landing page,” White mentioned.
What the Unit 42 analysis effort discovered was that the attackers had been utilizing compromised websites as half of a bigger rip-off involving internet online affiliate marketing ways. In the rip-off, customers are tricked into clicking a hyperlink, which is then handed via a number of layers of redirection earlier than hitting the ultimate touchdown web page. On the touchdown web page, customers are tricked into signing up for subscriptions and different undesirable objects.
The exact variety of people who clicked on the assorted affiliate fraud spam campaigns just isn’t identified, although Unit 42’s analysis estimates that on common every hyperlink it discovered was clicked 273 occasions. Across the 15,000 subdomains concerned, that interprets into probably tens of millions of impacted customers.Takedown
After White and the Unit 42 analysis workforce made GoDaddy conscious of the state of affairs, GoDaddy labored to take down the 15,000 subdomains.
“We did not engage any law enforcement, nor did GoDaddy,” he mentioned. “GoDaddy was able to take action due to the unauthorized access and usage of their customer accounts.”
The varied internet online affiliate marketing campaigns for weight-loss and different merchandise that White tracked usually are not a uncommon phenomenon on the fashionable web. White mentioned there are a number of…