Security researcher Victor Gevers, co-founder of the GDI Foundation, a non-profit dedicated to making the internet safer, is urging administrators to check their MongoDB installations, after finding nearly two hundred of them wiped and being held for ransom.
On Monday morning, Gevers said he’d discovered 196 instances of a MongoDB installation exposed to the public that’s been erased and held for ransom. UPDATE: The count reached nearly 2,000 databases as of 4:00 p.m.
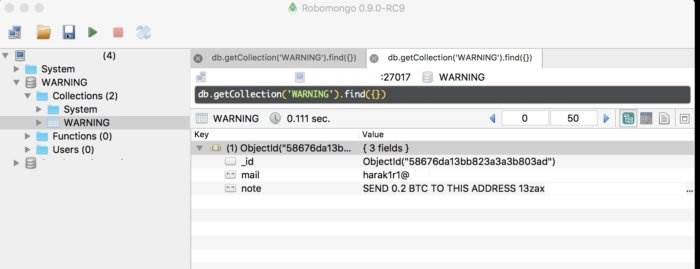
The person behind the attacks is demanding 0.2 BTC ($202.89) as payment, and requiring system administrators email proof of ownership before the files are restored. Those without backups are left in a bind.
Gevers has sent dozens of notifications to affected victims and on Twitter has responded to at least two requests for assistance after administrators learned of the issue.
In each observed attack, the message remains the same – pay up or lose your data. It’s possible the attacker is finding open MongoDB installs via basic scanning or Shodan, Gevers said. It’s also possible they’re finding MongoDB installs that are vulnerable to various exploits, including one that allows remote authenticated users to obtain internal system privileges.
 Victor Gevers / SRAGAN
Victor Gevers / SRAGANIf so, then administrators are caught in the middle of a rat race between Gevers and “Harak1r1” – the person responsible for the attacks. Asked for his thoughts and advice, Gevers shared the notification letter he is sending to identified victims.
In it, he advises that they protect the MongoDB installs by blocking access to port 27017 or limit access to the server by binding local IPs. Administrators can also chose to restart the database with the “–auth” option, after they’ve assigned users access.
In addition, he offers the following tips:
- Check the MongDB accounts to see if no one added a secret (admin) user.
- Check the GridFS to see if someone stored any files there.
- Check the logfiles to see who accessed the MongoDB (show log global command).
“Criminals often target open databases to deploy their activities like data theft/ransom. But we also have seen cases were open servers like these are used for hosting malware (like ransomware), botnets and for hiding files in the GridFS,” the notification letter explains.
In late 2015, there were approximately 35,000 MongoDB installations on the internet. Most of these installations were insecure and publicly available, and combined stored nearly 700TB of data.
Configuration errors in MongoDB have led to a number of major data breaches, including the Hello Kitty data breach that exposed 3.3 million people.
A short time later, CSO Online was the first to report on the existence of an exposed MongoDB that contained 191 million voter records with the help of researcher Chris Vickery and Databreaches.net.
This was followed by a story detailing the existence of a second voter database a week later. Last April, a poorly configured MongoDB installation exposed the personal details on 93 million Mexican voters.
MongoDB is a favorite among some IT professionals, but if it isn’t configured properly and secured, this popular platform can be the source of a lot of pain within an organization. The official documentation for MongoDB contains a security checklist, and administrators are encouraged to follow it completely.
This story, “Exposed MongoDB installs being erased, held for ransom” was originally published by
CSO.