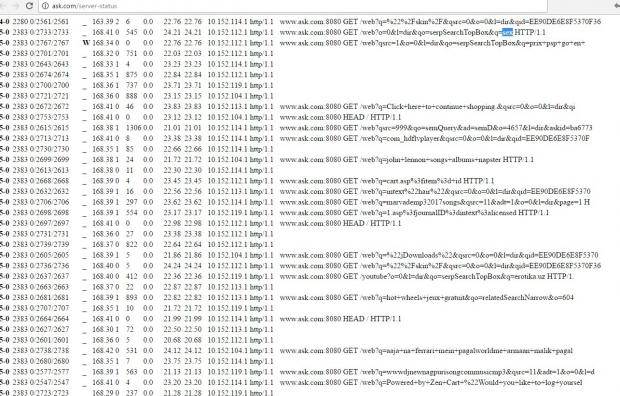
Ask.com’s Apache server status page is open to the public, and everyone can see what people are searching for. Any queries and user actions done on that particular server on Ask.com are open to anyone who wants to have a look.
The discovery was made by researcher Paul Shapiro earlier today, and even though it’s been a couple of hours since the revelation was made, Ask.com has not hidden its server from people’s eyes.
It’s unclear for how long this page has been open to the public, and given Ask.com’s inaction, neither is for how long it’s going to be left like this. The server status page was restarted over three days ago, and the running theory is that during that reboot the server page was accidentally left exposed.
There are also details regarding the total accesses since the server reset – 4.4 million, the total traffic – 237.9 GB, and so on.

Not a security threat
Thankfully, while it’s pretty clear that people are looking for things like the iPhone 4’s processor speed, how to prepare your wedding, John Lennon’s songs and albums on Napster, and Home Depot coupon for new movers, these people’s IP addresses aren’t revealed in the process. In fact, all the IP addresses listed are internal IPs, which Search Engine Land says are likely Ask.com’s firewall. User queries, however, can be followed in real time.
This data leak is worrisome, but at the very least, those personal IP addresses are hidden from prying eyes. It is particularly because of this reason only that the leaky server logs aren’t a major security threat. It’s not exactly common practice for such details to be left exposed for everyone to see. Hopefully, the leak will be plugged soon, and Ask.com will actually say something on the matter. Until then, you can just refresh the page to see the latest queries.
Oh gosh! https://t.co/ArNClLQsly is leaking its server logs. Look at what people are searching: https://t.co/wy08gSrgwq
— Paul Shapiro (@fighto) April 7, 2017