Network security firm Neustar says that around 80 percent of DNSSEC servers have been improperly configured, and attackers can hijack them to carry out above-average reflection DDoS attacks
DNSSEC is an extension of the DNS protocol that uses digital signatures to authenticate and verify DNS queries.
DNSSEC is the recommended DNS implementation to deploy on modern servers, but just like any other product that employs cryptographic operations, webmasters can sometimes muddle up the process and leave servers vulnerable after getting them to run.
Number of DNSSEC-based DDoS attacks is on the rise
DNSSEC was not intended to protect against attackers hijacking servers for reflection DDoS attacks. Security experts recommend that webmasters deploy DNSSEC to protect against DNS hijacking and DNS cache poisoning attacks.
As companies started deploying this DNS protocol extension, network security firms began to see more attacks using this vector. The first to report on this rising trend was Akamai, who said at the start of the year that it detected over 400 reflection DDoS attacks in Q4 2015.
After seeing a rise in DNSSEC-based DDoS attacks itself, Neustar analyzed over 1,349 domains that use DNSSEC from just one industry vertical.
Neustar researchers discovered that 1,084 of the analyzed domains contained vulnerabilities that allowed attackers to use DNSSEC to reflect and amplify their DDoS attacks.
Attackers exploit DNSSEC ANY command
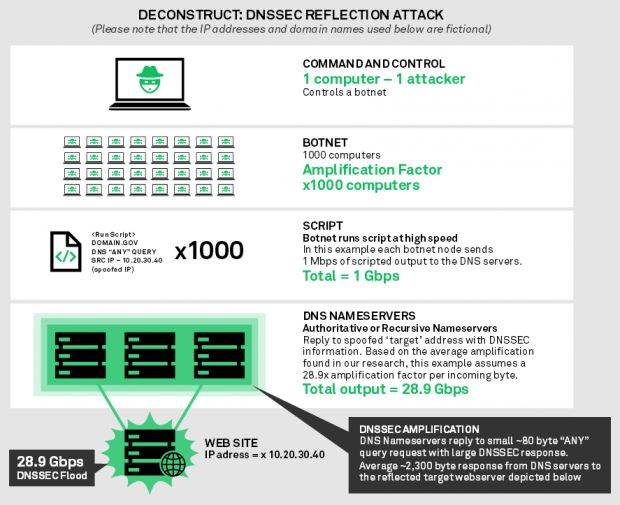
Researchers say that attackers send DNSSEC requests to a domain name server signed with the ANY command, which forces the DNSSEC server to gather all the DNS info about that domain and respond to the query.
Additionally, the server will attach its digital signature to the response, adding more weight to the DNS server response.
Because DNSSEC server queries can be spoofed with a fake sender IP address, the attackers are tricking the server into responding to the victim’s IP address, sending junk traffic to the wrong person (the target of the DDoS attack).
Neustar explains that it costs an attacker only 80 bytes to send the initial DNSSEC query, but the server would reply (because of the ANY command) with a minimum of 2,313 bytes, the size of a basic ANY-based DNSSEC response.
Of course, based on the information included in the response, the return packet would sometimes have a bigger size. Neustar reported seeing some servers responding to specific domains with responses as big as 17,377 bytes.
DNSSEC DDoS attacks have an above-average amplification factor
This means that a DNSSEC-based reflection DDoS attack has an amplification factor that ranges from 28.9 to a whopping 217.2. The average amplification factor for reflection DDoS attacks is around 10, making DNSSEC a clear-cut favorite for running such attacks.
Taking into account that around 80 percent of DNSSEC servers are improperly configured, attackers have a huge attack surface to work with for their operations, which also explains why more and more DDoS tools will exploit it, as more DNS servers start deploying DNSSEC.
To mitigate the possibility of having their server hijacked for DDoS attacks, webmasters should configure DNSSEC servers to ignore DNS queries with the ANY parameter.
Neustar’s DNSSEC: How Savvy Attackers Are Using Our Defenses Against Us report is available for download if you want to take a closer look at how DNSSEC DDoS attacks work.





![[Interview] [Galaxy Unpacked 2026] Maggie Kang on Making](https://loginby.com/itnews/wp-content/uploads/2026/02/Interview-Galaxy-Unpacked-2026-Maggie-Kang-on-Making-100x75.jpg)